Numerous suppliers of programming as-a-administration (SaaS) applications need to reach however many various clients as could reasonably be expected to scale their contribution while streamlining cost and functional proficiency. Accomplishing this while meeting security prerequisites and client highlight requests can challenge.
Utilizing a serverless model where you can depend on oversaw administrations and exact scaling of assets without the need to spend in pre-speculations is a convincing fit for a SaaS application.
This post expands upon the center ideas introduced in Building a Multi-Occupant SaaS Arrangement Utilizing AWS Serverless Administrations to propose a financially savvy pooled multi-occupant serverless design that gives:
Disconnection of occupant information.
Capacity for clients to have a place with different occupants.
Consistent exchanging between occupants for clients.
Custom client jobs with custom authorizations by occupant administrators.
56K.Cloud is an AWS Accomplice and driving counseling and designing firm giving turn-key arrangements. It practices on Amazon Web Administrations (AWS) all in all cycle from cloud warning and movement to prototyping and oversaw administrations. With a group with major areas of strength for an in application improvement, it has a profound mastery of serverless structures permitting it to direct its clients through building solid, secure and practical serverless applications like the one introduced here.
Arrangement Outline
The proposed multi-inhabitant engineering uses the accompanying oversaw administrations:
Amazon DynamoDB as an information base.
AWS Lambda for backend code, approval, and occupant organization inside the control plane.
Amazon Programming interface Door to make a REST Programming interface.
Amazon Cognito for personality the executives.
Safeguarding Information with Amazon DynamoDB
Amazon DynamoDB is a completely overseen NoSQL data set, known for cost-viability, versatility, and reliable execution. Legitimate information confinement between occupants is vital, and a solitary table plan where all application information is put away in one table offers a few benefits:
Decreased functional above; a solitary table to arrangement, and no different assets for new occupants.
Smoothed out include organizations and information base updates with a solitary data set.
Steady question execution through powerful information demonstrating for required admittance designs.
Depending just on application rationale for inhabitant seclusion conveys chances. Believing business rationale and data set inquiries alone doesn’t ensure inhabitant information detachment; an inadvertent application misconfiguration with unfortunate secondary effects could continuously escape everyone’s notice.
Setting AWS Personality and Access The executives (IAM) approaches on the DynamoDB table to authorize access controls gives an additional proportion of safety and reflects best practice guardrails to keep up with guideline of least restricted admittance.
DynamoDB gives a dynamodb:LeadingKeys condition which can be utilized to carry out column based admittance control by conceding admittance to just certain parcel keys.
Nonetheless, putting all occupant information inside a solitary parcel would mean a high volume of perused and compose solicitations to a solitary segment, which could cause undesirable choking (hot parts). IAM upholds trump cards for the dynamodb:LeadingKeys condition, meaning one could execute parcel key sharding where the information kept in touch with the table are spread equally across different allotments. This outcomes in better parallelism and higher by and large throughput while as yet having the option to get allotments.
A table’s essential list isn’t the sole access technique. Optional files, both nearby and worldwide, take special care of extra access designs. For example, to permit clients to have a place with numerous occupants, the essential file can have a one-to-many inhabitant to-client relationship (essential key TENANT#{tenant_id} and sort key USER#{user_id}).
A worldwide optional list can flip this to a one-to-numerous client to-inhabitant relationship (essential key USER#{user_id} and sort key TENANT#{tenant_id}). Auxiliary files can likewise be gotten by adding significant assets to the IAM strategy.
Character The board
Amazon Cognito is a character supplier contained two kinds of pools: client pools for confirming clients and putting away their properties; and personality pools for giving impermanent AWS qualifications to get to assets and administrations.
The primary objectives are:
Use Cognito as the sole personality supplier.
Give occupant checked admittance to the DynamoDB table.
Permit clients to have a place with various occupants.
The IAM strategy contains a PrincipalTag variable. While trading for certifications, this variable should be supplanted by the client’s inhabitant ID. The client pool is designed with a custom:tenant_id client trait. To plan this trait to the IAM PrincipalTag condition and serve impermanent inhabitant perused AWS accreditations, a personality pool is designed with:
The client pool as the character supplier
A custom case planning between the custom:tenant_id property and PrincipalTag variable.
Our IAM job as the verified job.
At this stage, we have a method for planning clients to an inhabitant and serving checked qualifications for them by means of the personality pool. Nonetheless, we want to meet the prerequisite of a many-to-numerous connection among clients and occupants. We propose utilizing Cognito client gatherings, where each occupant has a relating bunch and Cognito permits clients to have a place with numerous gatherings. Moreover this approach permits Cognito client gatherings to show up in the ID token.
Since a client can have a place with different inhabitants, the custom:tenant_id characteristic should be changeable to demand perused certifications for the pertinent occupant. In any case, the Cognito Application Client utilized by the frontend ought to need compose honors on this delicate characteristic; just the control plane Lambda ought to have compose access.
Confirmation Streams
To give additional background info of how the above ideas cooperate, we should go over key client streams of a multi-occupant application.
New client join.
Account affirmation through SMS or email code.
Upon affirmation, a Lambda trigger saves the client’s profile data to DynamoDB, as Cognito ought not be utilized as an essential datastore.
Amazon Cognito returns an ID token for the frontend application to confirm Programming interface demands.
Frontend application presents a structure to make another occupant, calling the make inhabitant Programming interface with the ID token and occupant subtleties.
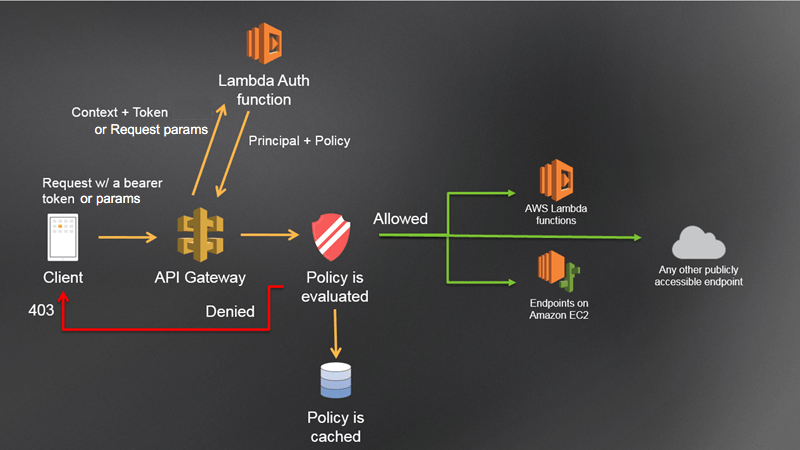
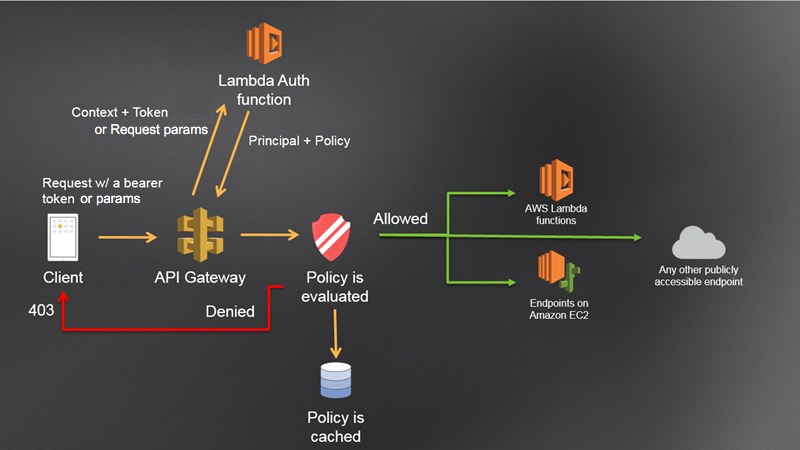
Amazon Programming interface Passage’s Lambda authorizer approves the client’s personality utilizing the ID token and, upon progress, plays out the accompanying undertakings: a. Make irregular occupant ID. b. Make new occupant segment in DynamoDB. c. Make another gathering in the Cognito client pool with the Occupant ID as name. d. Add the client to the gathering. e. Update the client’s Occupant ID property in the client pool. f. Call the InitiateAuth Programming interface with REFRESH_TOKEN_AUTH to get new tokens for our client’s refreshed status.
New tokens are returned for ensuing Programming interface calls.
Checked Information base Access
Unraveling the ID token uncovers its ascribes line up with Cognito settings:
cognito:groups: rundown of client’s subsidiary gatherings.
custom:tenant_id: ID of client’s dynamic inhabitant.
The Programming interface endpoints dealing with Muck information base tasks depend on a Lambda authorizer that does the accompanying:
Approves the ID token’s mark
Use Cognito’s GetCredentialsForIdentity to gain fleeting access qualifications in view of the ID token and personality pool’s validated job.
Returns accreditations, occupants, and client IDs in the authorizer reaction setting object as key-esteem matches.
After effective verification, Amazon Programming interface Door sends the approval setting with AWS qualifications to your Lambda capability, permitting it to instate the DynamoDB SDK and settle on data set decisions confined to the client’s authorizations.
Exchanging Between Occupant Conditions
SaaS applications frequently empower clients to switch between numerous associations, and the proposed design works with this by permitting clients to change their dynamic inhabitant.
The custom tenant_id Cognito client quality was characterized as changeable, meaning the control plane Lambda can utilize the UpdateUserAttributes Programming interface to refresh it. This is a delicate activity and ought to possibly find success in the event that the client has a place with the mentioned occupant by cross-referring to against the client’s Cognito Client Gathering participation. On progress, Cognito issues another ID token for Programming interface calls, and data set activities are checked to the new Occupant ID.
Client needs to change dynamic occupants: the application recovers the rundown of inhabitants the client is an individual from DynamoDB utilizing a worldwide optional list with the one-to-numerous client to inhabitant relationship.
Application shows the rundown of occupants in a menu.
Client chooses Occupant B, setting off a Programming interface call to change the client’s dynamic occupant, passing Inhabitant B’s ID in the payload.
The authorizer approves the JWT ID token, removes the cognito:groups guarantee containing the client’s gatherings, and passes the rundown back in the authorizer’s reaction.
Lambda confirms that Occupant B’s ID is remembered for the gathering list, refreshes the client’s occupant ID trait in the client pool by having administrator admittance to Cognito, and afterward revives the client’s tokens.
Revived tokens are returned in the Programming interface reaction.
Resulting Programming interface demands by the application will be checked to Inhabitant B.
Custom Jobs for Explicit Occupant Conditions
Up to this point, we’ve zeroed in on restricting admittance to occupant information. Be that as it may, imagine a scenario in which we need to give clients opportunity to make their own jobs and consents inside their association.
An expansion of Cognito client gatherings, IAM jobs, and strategies isn’t reasonable, and you risk arriving at IAM and Cognito asset quantities. Besides, IAM strategies have no control over admittance to DynamoDB sort keys, an essential DynamoDB include.

